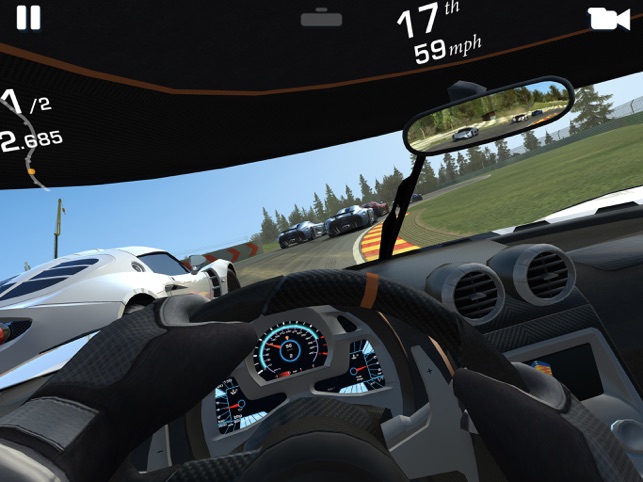
Time Attack in Need for Speed (2015) is a racer versus racer lap time event type along a route set out with checkpoints. The participant with the fastest lap time around the set route, once the event time has run out, is the winner. Need for Speed Payback. Videogameasset My games. When logged in, you can choose up to 12 games that will be displayed as favourites in this menu. Recently added 21 View all 1,173. Log in to view your list of favourite games.
- Need For Speed Payback Mac Attack Download
- Need For Speed Payback 2
- Need For Speed Payback Mac Attack Simulator
- Need For Speed Payback Pc
- Need For Speed Payback Wiki
Severity: Important
CVSS Score: 7.8
Impact: Elevation of Privilege
Status: Fixed
Affected Software: Origin for Mac & PC version 10.5.74.41754 (or earlier)
Description
A vulnerability exists in the Origin Client Service that could allow a non-Administrative user to elevate their access to System. Once the user has obtained elevated access, they may be able to take control of the system and perform actions otherwise reserved for high privileged users or system Administrators.
Attack Scenario
To successfully leverage the vulnerability, the attacker needs to have valid user credentials with the ability to log-on to the computer that has the Origin Client installed. Upon successfully logging in the attacker would then need to be able to install a specially crafted program or execute code that modifies the contents of affected Origin install directories. They would then need to stop and restart the Origin Client.
Mitigations
Mitigations describe factors that limit the likelihood or impact of an attacker successfully leveraging the vulnerability
- A successful attack would require the user of a valid account on the local machine with the Origin Client installed.
Need For Speed Payback Mac Attack Download
Workarounds
Workarounds are steps EA customers can take to reduce the potential for an attacker to leverage the vulnerability if they cannot or choose not to install the update.

- In order to temporarily limit the likelihood of the vulnerability being executed by non-privileged users, the system administrator may choose to remove local login rights from accounts or disable non-administrator accounts.
Resolution
To address the vulnerability players with Administrator rights are advised to install the latest version of the Origin Client version 10.6.0.42339.
On the next player login, the player will be required to update before entering their credentials. If they are already logged in, they will need to restart Origin to get the update.

Frequently Asked Questions:
How is Issue Severity Determined?
Issue severity is based on a 4-point scale ranging from Critical to Low. As part of our investigation, security engineers determine the overall ease of exploitation and how an attacker would need to successfully exploit the vulnerability. Typically, the fewer barriers that exist to exploitation combined with a higher Security Impact, the higher the Issue Severity designation.
What causes the vulnerability?
The vulnerability is caused by the Origin Client Service’s loading of 3rd party plugins. In this scenario, a specially crafted QT plugin could potentially be loaded running under the context of System. This would enable a standard user to elevate to Administrator or System privileges and potentially take full control of the affected system.
What is Qt?
Qt is a free and open-source widget toolkit for creating graphical user interfaces as well as cross-platform applications that run on various software and hardware platforms.

How do I know if I am vulnerable?
If Origin client version 10.5.74.41754 or earlier is installed on the system, it is vulnerable to this issue.
How does the update resolve the vulnerability?
The update restricts the dynamic loading of 3rd party plugins to the application directory. This directory is only editable by an Administrator account.
Has this vulnerability been used against EA’s customers?
No. At the time of publication of this advisory we are not aware of any attacks against EA’s players that leverage this vulnerability.
Acknowledgement(s)
EA thanks the following security researcher for their discovery and reporting it to us in accordance with Coordinated Vulnerability Disclosure practices:

Need For Speed Payback 2
- Joel Noguera of Immunity Inc for reporting CVE-2020-15524
Need For Speed Payback Mac Attack Simulator
Need For Speed Payback Pc
Date Published: 7/22/2020
Need For Speed Payback Wiki
Version: 1.0